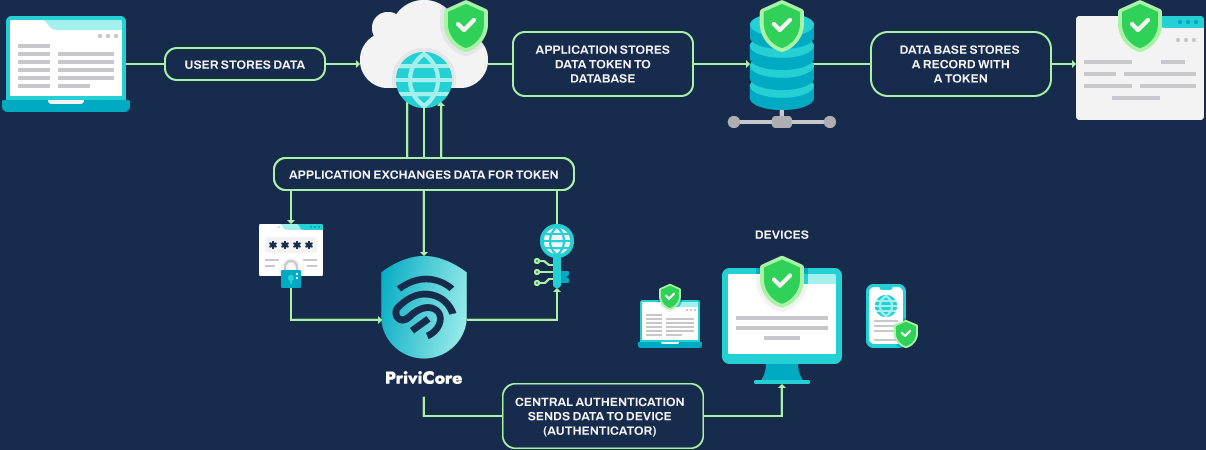
Typical process today

Use of the PriviCore
What sets us apart is our commitment to seamless integration. Our engine can work silently in the background, providing the security you need without interrupting the user’s workflow. It’s all about finding the right balance between protection and usability.
Experience Enhanced Protection:
Build Trust:
Ensure Compliance:
Scale with Ease:
PriviCore seamlessly integrates into your existing infrastructure, providing scalability and compatibility across systems, saving you time and resources.



