Can You Afford a Data Breach?
Could your business recover from that?
Relying on Perimeter Protection? Your Data Needs More
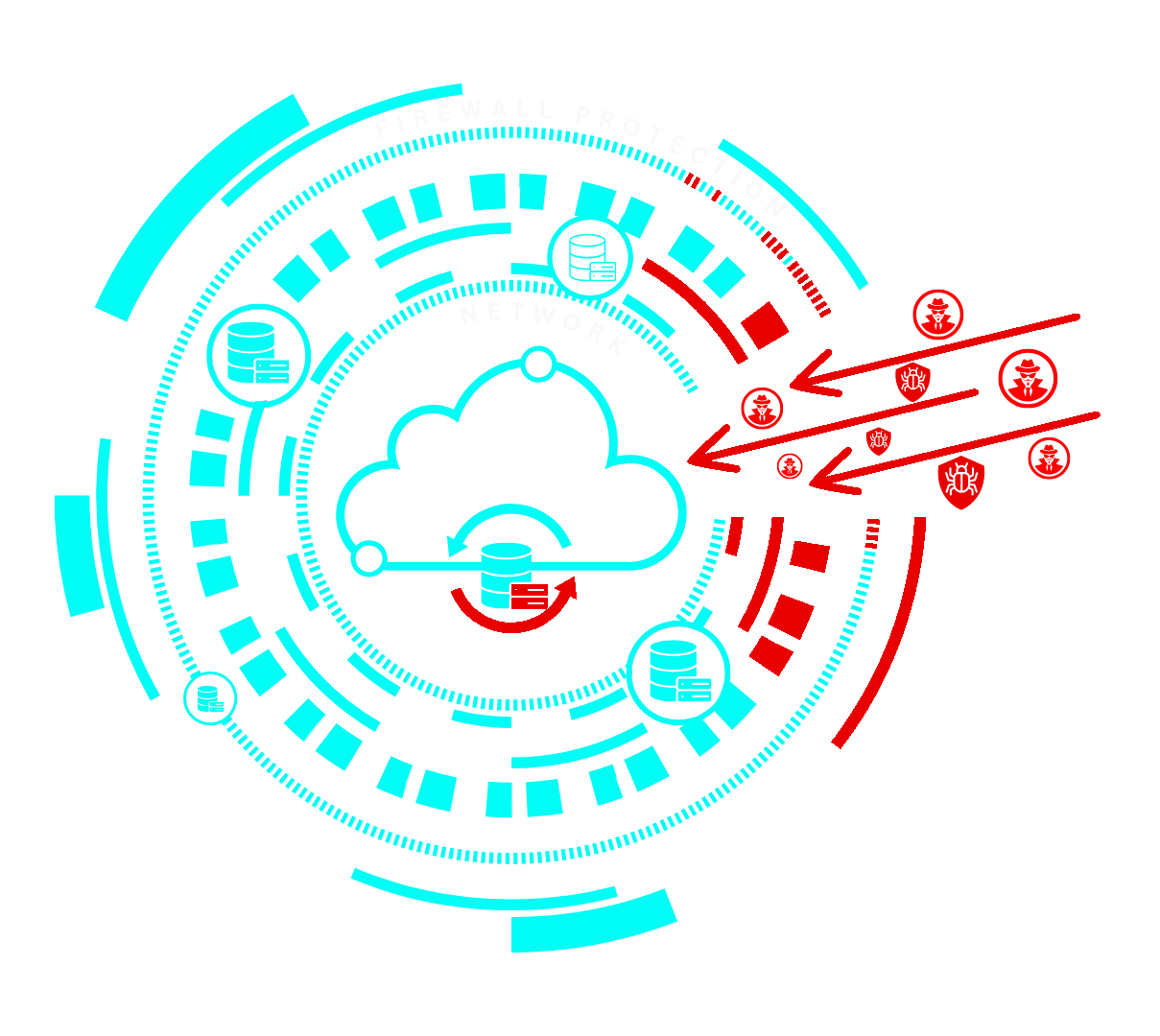
Each time a hack is blocked, attackers adapt and improve their methods, increasing the likelihood of eventual success. This continuous cycle makes traditional defenses less effective over time. Relying solely on perimeter protection can create a false sense of security, highlighting the need for layered, adaptive security measures.
Solution
Protect data easily with the Privicore Data Privacy Platform, designed to work smoothly with your R&D teams
Our APIs provide multi-layer encryption, tokenization, and secure multi-storage—whether in cloud or on-premise. With a robust policy and voting engine, your sensitive data remains protected at every stage: at rest, in use, and in motion.
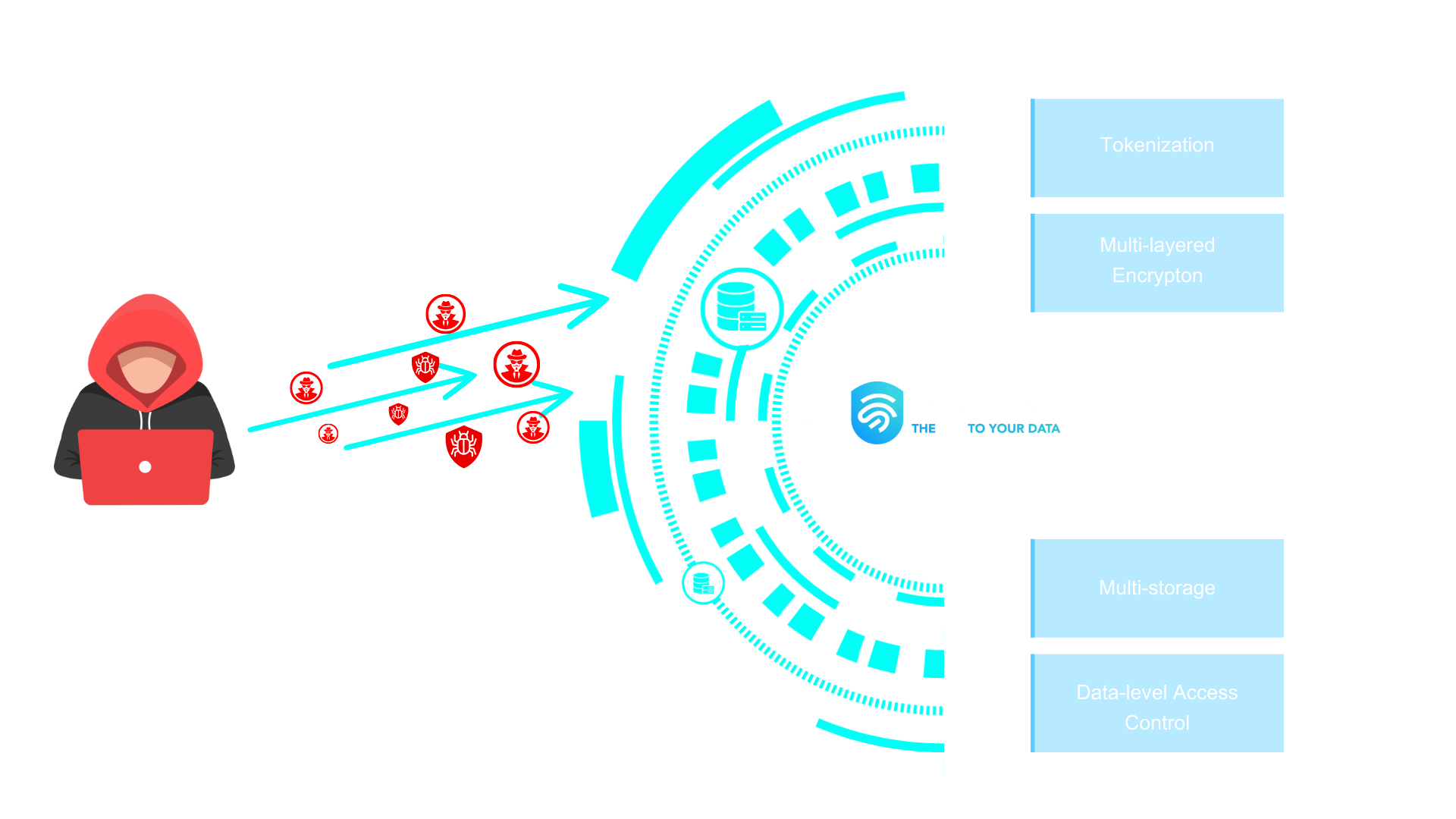
End-to-end Data Security in One Platform
Data Privacy Manager (DPM)

Multi Cloud
Databases
Files
Applications
Documents
Back-ups
Ransomware Defense
Data is tokenized and stored in multiple locations, making it nearly impossible for attackers to breach all at once.
Data Loss Prevention
Storing data across different sources significantly reduces the risk of loss.
Unreadable to Intruders
Multiple encryption layers and separate key storage keep data unreadable, even if breached.
Controlled Data Access
Strict access control using trusted devices, biometrics, and location ensures that only authorized users can access data.
Connect
Gather your API details and get ready to start.
Register
Create your application profile in minutes.
Authenticate
Secure your connection with an authorization token.
Tokenize
Protect your data by converting it into secure tokens.
Access & Manage
Retrieve data securely and monitor everything with ease.
Technology Behind PriviCore
Key Management
Without keys, data can’t be decrypted. We store them in multiple locations for added security.
Fast Encryption technology
In combination with tokenization we use a fast and secure elliptic curve encryption method to encrypt data.
Tokenization
Sensitive data like credit card numbers are replaced with tokens, useless to hackers.
Policy & Voting
Device security
Use of an immutable ledger ensures device security and trust.
Storage Decentralization
We separate data storage from encryption keys, reducing the risk of breaches and ransomware.
AI & Machine learning
Policy based learning algorithms and risk profiling.
Secret management & Synchronization
Manage all client’s secret and synchronize data across storage devices.
High transaction volume using Fast Message Queue
Fast acceleration for low latency and fast transactions.